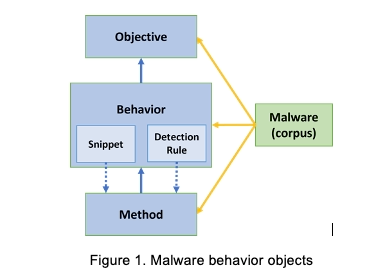
I recently saw a few malware-behaviour objects in a STIX bundle.
{
"type": "bundle",
"id": "bundle--6b32c658-f907-4a02-bd68-d971d0c83822",
"objects": [
{
"type": "malware-behavior",
"spec_version": "2.1",
"id": "malware-behavior--0a11a488-9138-4341-a879-32a2c251e01f",
"created_by_ref": "identity--b73c59c1-8560-449a-b8d0-c2ce0533c5bf",
"created": "2020-08-14T00:00:00.000Z",
"modified": "2023-12-05T00:00:00.000Z",
"name": "Heap Spray",
"obj_defn": {
"description": "Malware may use heap spraying to write a sequence of bytes on the heap section of a process.",
"external_id": "C0006",
"source_name": "mitre-mbc",
"url": "https://github.com/MBCProject/mbc-markdown/blob/main/micro-behaviors/memory/heap-spray.md"
},
"objective_refs": [
"malware-objective--dbe27c30-ea5f-44a0-9167-ead41fc8d420"
],
"obj_version": "2.1",
"object_marking_refs": [
"marking-definition--093b6375-cd45-4aa3-8f91-6a03ddd7a3d3"
],
"extensions": {
"extension-definition--d57b7c9c-7fa6-436b-b82c-8e6f69cdc3d0": {
"extension_type": "new-sdo"
}
}
}
]
}
Using the url listed in the object, I found this repo
The MBC project looks very interesting. Is anyone using it with STIX? If so, do you have any guides to get started?