Hey @0101001001001 ,
You’re soooooo close 
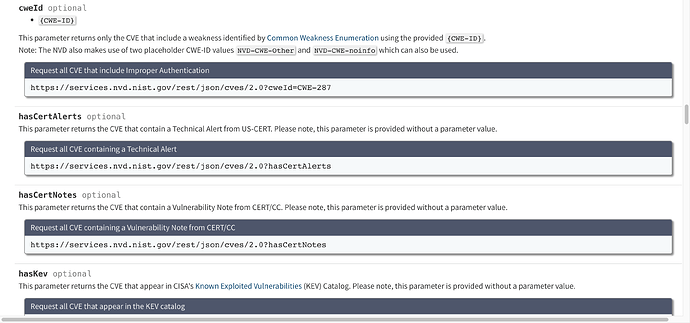
The hasCertNotes and hasCertAlerts properties are not boolean. You just need to pass them with a null value to get a response.
https://nvd.nist.gov/developers/vulnerabilities
e.g.
curl --location 'https://services.nvd.nist.gov/rest/json/cves/2.0?hasCertAlerts=&lastModStartDate=2024-01-01T00%3A00%3A00.000&lastModEndDate=2024-01-31T23%3A59%3A59.000' \
--header 'apiKey: REDACTED'
{
"resultsPerPage": 5,
"startIndex": 0,
"totalResults": 5,
"format": "NVD_CVE",
"version": "2.0",
"timestamp": "2024-06-05T11:18:32.650",
"vulnerabilities": [
{
"cve": {
"id": "CVE-1999-0067",
"sourceIdentifier": "cve@mitre.org",
"published": "1996-03-20T05:00:00.000",
"lastModified": "2024-01-26T20:00:52.747",
"vulnStatus": "Analyzed",
"descriptions": [
{
"lang": "en",
"value": "phf CGI program allows remote command execution through shell metacharacters."
}
],
"metrics": {
"cvssMetricV2": [
{
"source": "nvd@nist.gov",
"type": "Primary",
"cvssData": {
"version": "2.0",
"vectorString": "AV:N/AC:L/Au:N/C:C/I:C/A:C",
"accessVector": "NETWORK",
"accessComplexity": "LOW",
"authentication": "NONE",
"confidentialityImpact": "COMPLETE",
"integrityImpact": "COMPLETE",
"availabilityImpact": "COMPLETE",
"baseScore": 10.0
},
"baseSeverity": "HIGH",
"exploitabilityScore": 10.0,
"impactScore": 10.0,
"acInsufInfo": false,
"obtainAllPrivilege": true,
"obtainUserPrivilege": false,
"obtainOtherPrivilege": false,
"userInteractionRequired": false
}
]
},
"weaknesses": [
{
"source": "nvd@nist.gov",
"type": "Primary",
"description": [
{
"lang": "en",
"value": "CWE-78"
}
]
}
],
"configurations": [
{
"nodes": [
{
"operator": "OR",
"negate": false,
"cpeMatch": [
{
"vulnerable": true,
"criteria": "cpe:2.3:a:apache:http_server:1.0.3:*:*:*:*:*:*:*",
"matchCriteriaId": "B5EA86B9-4F86-4ADA-BC6A-4F6E261848F6"
},
{
"vulnerable": true,
"criteria": "cpe:2.3:a:ncsa:ncsa_httpd:1.5a:*:export:*:*:*:*:*",
"matchCriteriaId": "7D7735EC-8C34-4C2B-B8CC-154182D070C2"
}
]
}
]
}
],
"references": [
{
"url": "http://www.cert.org/advisories/CA-1996-06.html",
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory",
"US Government Resource"
]
},
{
"url": "http://www.osvdb.org/136",
"source": "cve@mitre.org",
"tags": [
"Broken Link"
]
},
{
"url": "http://www.securityfocus.com/bid/629",
"source": "cve@mitre.org",
"tags": [
"Broken Link",
"Third Party Advisory",
"VDB Entry"
]
}
]
}
},
You know they’re related to CertAlerts or CertAlerts (if not using these filters) b/c the references.tags property of the CVE will contain US Government Resource
e.g.
"tags": [
"Broken Link",
"Third Party Advisory",
"US Government Resource"
]