Ah good spot. I never noticed this.
Debugging
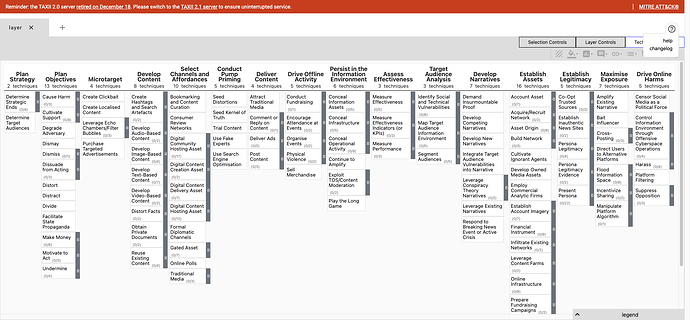
At first I thought the order was determined by the Tactic ID (numerical order)
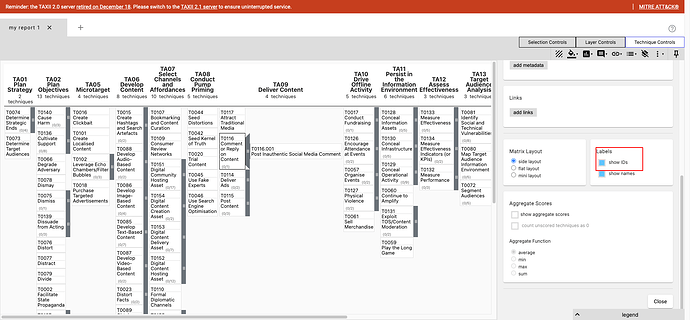
(click Technique Controls and Show IDs)
However, that’s not true. Look at ATT&CK
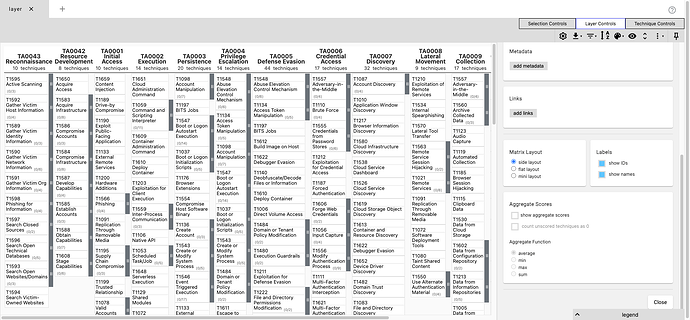
TA0043 comes before TA0001
So I examined the ATTT&CK Tactics in more detail;
curl -X 'GET' \
'https://api.ctibutler.com/v1/attack-enterprise/objects/?type=x-mitre-tactic' \
-H 'accept: application/json' \
-H 'API-KEY: REDACTED'
{
"page_size": 50,
"page_number": 1,
"page_results_count": 14,
"total_results_count": 14,
"objects": [
{
"created": "2018-10-17T00:14:20.652Z",
"created_by_ref": "identity--c78cb6e5-0c4b-4611-8297-d1b8b55e40b5",
"description": "The adversary is trying to steal account names and passwords.\n\nCredential Access consists of techniques for stealing credentials like account names and passwords. Techniques used to get credentials include keylogging or credential dumping. Using legitimate credentials can give adversaries access to systems, make them harder to detect, and provide the opportunity to create more accounts to help achieve their goals.",
"external_references": [
{
"external_id": "TA0006",
"url": "https://attack.mitre.org/tactics/TA0006",
"source_name": "mitre-attack"
}
],
"id": "x-mitre-tactic--2558fd61-8c75-4730-94c4-11926db2a263",
"modified": "2022-04-25T14:00:00.188Z",
"name": "Credential Access",
"object_marking_refs": [
"marking-definition--fa42a846-8d90-4e51-bc29-71d5b4802168"
],
"spec_version": "2.1",
"type": "x-mitre-tactic",
"x_mitre_attack_spec_version": "2.1.0",
"x_mitre_domains": [
"enterprise-attack"
],
"x_mitre_modified_by_ref": "identity--c78cb6e5-0c4b-4611-8297-d1b8b55e40b5",
"x_mitre_shortname": "credential-access",
"x_mitre_version": "1.0"
},
Which has no more data to determine order than DISARM
curl -X 'GET' \
'https://api.ctibutler.com/v1/disarm/objects/?type=x-mitre-tactic' \
-H 'accept: application/json' \
-H 'API-KEY: REDACTED'
{
"page_size": 50,
"page_number": 1,
"page_results_count": 16,
"total_results_count": 16,
"objects": [
{
"created": "2020-01-01T00:00:00.000Z",
"created_by_ref": "identity--8700e156-6ce9-5090-8589-f9d0aef7bdb7",
"description": "Define the desired end state, i.e. the set of required conditions that defines achievement of all objectives.",
"external_references": [
{
"source_name": "DISARM",
"url": "https://raw.githubusercontent.com/DISARMFoundation/DISARMframeworks/main/generated_pages/tactics/TA01.md",
"external_id": "TA01"
}
],
"id": "x-mitre-tactic--b977ad29-eb0c-5f09-bb2f-6d3f23e2a175",
"modified": "2024-08-07T00:00:00.000Z",
"name": "Plan Strategy",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487",
"marking-definition--8700e156-6ce9-5090-8589-f9d0aef7bdb7"
],
"spec_version": "2.1",
"type": "x-mitre-tactic",
"x_mitre_shortname": "plan-strategy"
},
So I then took a look at the Matrix objects in ATT&CK
curl -X 'GET' \
'https://api.ctibutler.com/v1/attack-enterprise/objects/?type=x-mitre-matrix' \
-H 'accept: application/json' \
-H 'API-KEY: REDACTED'
{
"page_size": 50,
"page_number": 1,
"page_results_count": 1,
"total_results_count": 1,
"objects": [
{
"created": "2018-10-17T00:14:20.652Z",
"created_by_ref": "identity--c78cb6e5-0c4b-4611-8297-d1b8b55e40b5",
"description": "Below are the tactics and technique representing the MITRE ATT&CK Matrix for Enterprise. The Matrix contains information for the following platforms: Windows, macOS, Linux, AWS, GCP, Azure, Azure AD, Office 365, SaaS.",
"external_references": [
{
"external_id": "enterprise-attack",
"source_name": "mitre-attack",
"url": "https://attack.mitre.org/matrices/enterprise"
}
],
"id": "x-mitre-matrix--eafc1b4c-5e56-4965-bd4e-66a6a89c88cc",
"modified": "2022-04-01T20:43:55.937Z",
"name": "Enterprise ATT&CK",
"object_marking_refs": [
"marking-definition--fa42a846-8d90-4e51-bc29-71d5b4802168"
],
"spec_version": "2.1",
"tactic_refs": [
"x-mitre-tactic--daa4cbb1-b4f4-4723-a824-7f1efd6e0592",
"x-mitre-tactic--d679bca2-e57d-4935-8650-8031c87a4400",
"x-mitre-tactic--ffd5bcee-6e16-4dd2-8eca-7b3beedf33ca",
"x-mitre-tactic--4ca45d45-df4d-4613-8980-bac22d278fa5",
"x-mitre-tactic--5bc1d813-693e-4823-9961-abf9af4b0e92",
"x-mitre-tactic--5e29b093-294e-49e9-a803-dab3d73b77dd",
"x-mitre-tactic--78b23412-0651-46d7-a540-170a1ce8bd5a",
"x-mitre-tactic--2558fd61-8c75-4730-94c4-11926db2a263",
"x-mitre-tactic--c17c5845-175e-4421-9713-829d0573dbc9",
"x-mitre-tactic--7141578b-e50b-4dcc-bfa4-08a8dd689e9e",
"x-mitre-tactic--d108ce10-2419-4cf9-a774-46161d6c6cfe",
"x-mitre-tactic--f72804c5-f15a-449e-a5da-2eecd181f813",
"x-mitre-tactic--9a4e74ab-5008-408c-84bf-a10dfbc53462",
"x-mitre-tactic--5569339b-94c2-49ee-afb3-2222936582c8"
],
"type": "x-mitre-matrix",
"x_mitre_attack_spec_version": "2.1.0",
"x_mitre_domains": [
"enterprise-attack"
],
"x_mitre_modified_by_ref": "identity--c78cb6e5-0c4b-4611-8297-d1b8b55e40b5",
"x_mitre_version": "1.0"
}
]
}
Looking at the order of items in tactic_refs the first item is x-mitre-tactic--daa4cbb1-b4f4-4723-a824-7f1efd6e0592 which is
curl -X 'GET' \
'https://api.ctibutler.com/v1/attack-enterprise/objects/?id=x-mitre-tactic--daa4cbb1-b4f4-4723-a824-7f1efd6e0592' \
-H 'accept: application/json' \
-H 'API-KEY: REDACTED'
{
"page_size": 50,
"page_number": 1,
"page_results_count": 1,
"total_results_count": 1,
"objects": [
{
"created": "2020-10-02T14:48:41.809Z",
"created_by_ref": "identity--c78cb6e5-0c4b-4611-8297-d1b8b55e40b5",
"description": "The adversary is trying to gather information they can use to plan future operations.\n\nReconnaissance consists of techniques that involve adversaries actively or passively gathering information that can be used to support targeting. Such information may include details of the victim organization, infrastructure, or staff/personnel. This information can be leveraged by the adversary to aid in other phases of the adversary lifecycle, such as using gathered information to plan and execute Initial Access, to scope and prioritize post-compromise objectives, or to drive and lead further Reconnaissance efforts.",
"external_references": [
{
"external_id": "TA0043",
"source_name": "mitre-attack",
"url": "https://attack.mitre.org/tactics/TA0043"
}
],
"id": "x-mitre-tactic--daa4cbb1-b4f4-4723-a824-7f1efd6e0592",
"modified": "2022-04-25T14:00:00.188Z",
"name": "Reconnaissance",
"object_marking_refs": [
"marking-definition--fa42a846-8d90-4e51-bc29-71d5b4802168"
],
"spec_version": "2.1",
"type": "x-mitre-tactic",
"x_mitre_attack_spec_version": "2.1.0",
"x_mitre_domains": [
"enterprise-attack"
],
"x_mitre_modified_by_ref": "identity--c78cb6e5-0c4b-4611-8297-d1b8b55e40b5",
"x_mitre_shortname": "reconnaissance",
"x_mitre_version": "1.0"
}
]
}
TA0043, Reconnaissance aka the first tactic column 
The result
The Tactic order in the Navigator is determined by the order the objects are found in the x-mitre-matrix objects tactic_refs property.
We will ship a fix for this in the disarm2stix code to account for this soon. Tracking here: